MCP vs. A2A and the Fight for AI Fluency
Protocols like MCP and A2A standardize AI agent communication, facilitating integration, security, and collaboration among models and tools, with industry backing despite ongoing development and emerging standards.
TECH INFRASTRUCTUREARTIFICIAL INTELLIGENCEAUTOMATIONTECHNOLOGY
Eric Sanders
7/12/20254 min read
MCP vs. A2A and the Fight for AI Fluency
Artificial-intelligence agents are slamming into a communication ceiling. I think they reason well enough, but the moment you ask them to work with real-world data or talk to each other, the process always seems to have the possibility to turn brittle, bespoke, or even slow. I’m convinced that the next leap in AI won’t come from bigger models either. I think it will come from a common language that lets those models plug into the messy systems we already run. Two rival protocols currently, Anthropic’s Model Context Protocol (MCP) and Google’s Agent-to-Agent (A2A), are racing to become that lingua franca. An article recently posted by 'TheRegister' made a great comparison to visualize this battle between protocols: “If MCP is like USB-C, then you can think of A2A a bit like Ethernet.” I took this and thought it captured the entire drama: USB-C and Ethernet both move bits, but they solve very different problems as MCP and A2A do.
MCP and A2A blueprints
MCP: the model–tool handshake - MCP standardizes the way a model asks an outside system (think SQL databases, Kubernetes clusters, billing APIs) to do something. It uses JSON-RPC over familiar transports such as HTTP or Server-Sent Events (SSE), and it publishes a manifest of every tool the model can call . In practice, MCP turns “call this weird internal API” into “call any API that follows the spec.”
Agents declare capabilities (“I can write to Postgres”).
They expose schemas so downstream tools can validate inputs.
Every request–response is stateless, keeping the protocol simple.
Security comes down to standard auth headers—no magic, but no surprises.
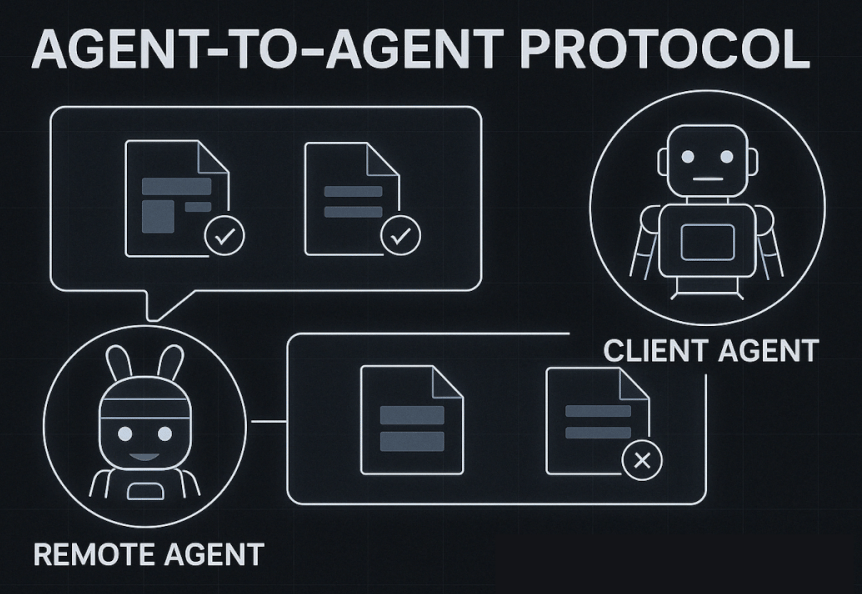
A2A: the Agent to Agent Switchboard
Google’s A2A begins one layer up though. It assumes every agent already knows how to hit a database. The hard part is getting a swarm of agents to cooperate. A2A opens with a discovery phase and a digital 'business-card' swap listing each agent’s name, endpoint, and authentication method before moving on to task delegation and real-time status updates. Some earlier posts found in a LinkedIn Post from CloudHa mentioned the following about A2A: “A2A empowers developers to build agents capable of connecting with any other agent built using the protocol and offers users the flexibility to combine agents from various providers.”
Discovery: swap capabilities and preferred data formats (text, image, audio, video).
Task creation: client agent sends work item; server agent replies with a task ID.
Progress tracking: polling or SSE pushes, depending on both sides’ support.
Artifacts: rich results—JSON, images, logs—returned under a single envelope.
The protocols look interchangeable on a slide deck but in the reality, they shape architecture choices available to us:
| Question | MCP’s answer | A2A’s answer |
| Who am I talking to? | A function or external service | Another autonomous agent |
| What’s negotiated? | Tool schema, auth, transport | Capabilities, roles, streaming mode |
| Success metric | Got the data / executed the call | Coordinated a multi-step workflow |
| Design risk | Leaky credentials or unsafe tool calls | Deadlocks, race conditions, partial failure |
You don’t pick one instead of the other. A production-grade agent may rely on MCP to fetch data, then fire an A2A message to a peer agent that handles orchestration or user notification.
Considerations for Builders Looking to Utilize A2A:
Model your ecosystem: List every API, database, and human queue an agent must touch. MCP removes glue code only if you actually document the tools.
Segment agent roles: Think microservices: a logging agent, a remediation agent, a billing agent. Smaller, single-focus agents fit A2A’s task-delegation model.
Adopt JSON-RPC conventions now: Both protocols lean on JSON-RPC. Enforce strict typing and error codes in your existing services so you’re not refactoring in a panic later.
Both protocols lean on JSON-RPC. Enforce strict typing and error codes in your existing services so you’re not refactoring in a panic later.
Design for failure transparency: A2A’s progress updates look optional, but long-running jobs will feel broken without them. Plan SSE endpoints and retry logic up front.
Map out security boundaries: MCP exposes tools; A2A exposes agents. Treat both as attack surfaces. Use signed capability manifests and rotate keys as aggressively as you do in zero-trust systems.
Turning standards into strategic leverage
A protocol is only as valuable as the network effects it unlocks. USB-C won because every laptop maker eventually got more from adopting it than from charging a licensing fee for a proprietary port. The same dynamic is playing out here:
Early adopters gain the right to plug in third-party agents without rewriting orchestration code—think Slack bots, finance bots, or a vendor’s LLM.
Tool vendors can ship one MCP adapter instead of 40 SDKs.
Cloud providers earn goodwill (and traffic) by hosting discovery registries or secure task routers.
The result is a flatter automation landscape where the best agent for a job wins on merit rather than on lock-in. If you build software for others, getting your name on the “supported” list for either protocol will soon be table stakes.
Where A2A May Run Into Roadblocks
Governance paralysis - Standards bodies move slower than startups. Competing task-ID formats or auth schemes could fragment implementations before they mature.
Security whiplash - Exposing a tool via MCP is handy until an over-permissive schema lets an agent drop tables. A2A’s discovery cards read like a menu for reconnaissance bots.
False equivalence - MCP and A2A solve different problems. Mashing them together without design discipline leads to spaghetti workflows that neither protocol can debug.
Mitigation starts with clear system boundaries and exhaustive unit tests that fire simulated MCP calls and A2A tasks under chaos conditions (latency spikes, revoked tokens, schema drift).
Where Do You Stand With A2A?
Will your next AI project speak the language of open protocols—or will it spend its life translating one-off scripts no one wants to maintain? How long can your stack stay competitive if every new agent arrives with a different dialect? The protocols are ready. The question is whether we, the builders, are bold enough to embrace them before the market makes the choice for us.
Efficiency
Transform your workflows and reclaim your time.
Contact Us
Need A Custom Solutions? Lets connect!
eric.sanders@thedigiadvantagepro.com
772-228-1085
© 2025. All rights reserved.
